The Washington Post called it, “The Year of Cybersecurity,” while very early on other media outlets were dubbing 2013, “The Year of the Hack.” Whatever you call it, 2013 brought a host of cybersecurity issues to the front of many legal and political debates. Since we are still freshly into the new year (and since this happens to be our 1000th post), I wanted to take a moment to review some of the bigger challenges faced by the international community in the cybersphere this past year.
U.S.-China Relationship
This crucial bilateral relationship was shaken when the United States accused China of launching cyber attacks on U.S. corporations, hacking into military and media networks, and engaging in cyberespionage against the United States. These allegations were vociferously denied by China. Soon thereafter, National Security Agency (NSA) contract employee Edward Snowden’s massive leak provided information backing a claim made by China that the U.S. had in fact hacked it rather than the other way around.
In an opinion piece by Dr. Cheng Li and Ryan McElveen of the Brookings’ John L. Thornton China Center, the authors argue,
U.S. technology firms conducting business in China . . . will never fully recover from the irreparable damage left by the devastating NSA revelations of 2013.
Earlier this year, “Zach,” a former blog contributor, posted links to a few great pieces published prior to the Snowden revelations and discussing the difficulty presented by Chinese cyberexploitation. In one, “Take Off the Kid Gloves and Stop China’s Cyber Thieves,” Liz Peek of The Fiscal Times argued that the U.S. has a difficult time “clamping down” on Chinese cyber theft because while U.S. corporations are the most damaged by China’s cyber activities, such entities are also dependent on the growth opportunities provided by China.
Syria
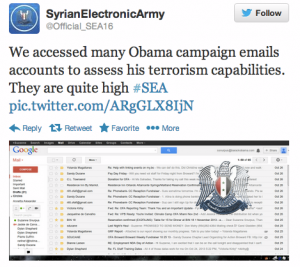
In support of President Bashar al Assad, the Syrian Electronic Army (SEA) hacked the Associated Press’s Twitter account this year and posted, “Breaking: Two Explosions in the White House and Barack Obama is Injured.” This headline sparked a stock exchange plunge whereby Dow Jones dipped 140 points before recovering following the Associated Press’s exposure of the hack. The SEA was also responsible for a number of freelance attacks, including taking responsibility toward the end of 2013 for hacking President Obama’s campaign emails and Twitter links, according to media outlets such as TechCrunch. Jillian York of the Electronic Frontier Foundation called SEA activities the “most intense cyberwarfare in the Arab world.”
Rise of Hackback
Vigilante-esque retaliatory action taken in cyberspace known as “hackback,” whereby a victim of a hack goes after the hacker, was a huge topic of conversation over the past year. Acknowledging that private firms are currently engaging in hackback with or without the legal authority to do so, some of the many issues raised included, whether the law should permit this activity and, if so, the type of regulatory regime that should accompany such a law.
Former blog contributor, “Zach,” proposed deputizing private companies under the Department of Justice (DOJ) through an amendment to the Computer Fraud and Abuse Act (CFAA) pursuant to which the DOJ would grant “hackback authorization” after a substantial Law of Armed Conflict-type analysis. He also provided a link early in the year to Adam Segal’s blog post on hackback discussing other issues that arise.
Later in the year, we saw other private players getting increasingly involved in this discussion, including Endgame creator, Chris Rouland, who lobbied at the Carnegie Council on Ethics in International Affairs for broader hackback authority.
Snowden and the NSA Revelations
As our readers know, Edward Snowden is the former NSA contractor responsible for disclosing classified NSA documents to the media, which revealed operational details of the NSA’s surveillance program, including its Bulk Telephony Metadata Collection Program.
On this topic, I focused mostly on the legal framework for the NSA’s Metadata Collection Program. From the Foreign Intelligence Surveillance Court (FISC) to various District Courts and references to Supreme Court precedent, we saw courts grapple with the Fourth Amendment, standing, and Section 215 of the Patriot Act. Some courts determined that the NSA had the authority to continue the program while others, most recently the D.C. District Court, deemed the NSA activities a likely violation of the Fourth Amendment. (Here are some of the posts with links to the court opinions: “District Court Grants Plaintiffs’ Motion for Preliminary Injunction Against NSA Surveillance Activities:” Part I, Part II, and Part III; “FISA Court Permits Controversial NSA Surveillance to Continue:” Part I and Part II; “FISA Court Releases Declassified Order Upholding NSA Phone Program”).
Our review of Snowden and the NSA activities also implicated NSA’s citing of Executive Order 12333 as authority for the program, which blog contributor “Benni” addressed just last month. Blog administrator “Prof. Snyder” also delved into some of Mr. Snowden’s comments to reporters. Specifically, as articulated by “Prof. Snyder,” Mr. Snowden “claims he did what he did, because of a non-existent duty to violate domestic laws that conflict with non-existent international law.”
Korean Peninsula
This year, South Korean banking institutions were hacked sparking South Korea’s Ministry of National Defense announcing its plans to “boost its own cyberwar forces and work and train more closely with U.S. forces on cyber issues . . . .” We also saw a series of North Korean threats to launch covert cyberwar.
Potential Fracturing of the Internet
A few months ago, I briefly addressed the potential fracturing of the World Wide Web and that, not only has such a trend been predicted by experts such as Google CEO, Eric Schmidt and former State Department official, Jared Cohen, but that we might already be experiencing the early stages of this break up.
Honors
Information security training organization SANS honored several actors and entities at the wrap of 2013 that made a difference in cybersecurity during the year. Among them were Todd Boudreau, who redesigned the Army Signal warrant officer structure; Major TJ O’Connor, who increased his team’s cyber capabilities at West Point; and, Alex Ruiz, an Immigration and Customs Enforcement (ICE) employee responsible for developing a cyberspace training program to boost awareness.
We were also proud to announce former blog contributor, “Zach,” won the 2013 Distinguished Legal Writing Award from a national organization for a paper he wrote on hackback.
With this in mind, some experts forecast increased issues with malware threats to mobile and cloud security. Of course, we will also likely continue to see the courts wrestle with the constitutionality of the NSA surveillance program.




Leave a Reply